
Amazon EFS (Elastic File System) is a serverless help given by Amazon to share a filesystem across various accessibility zones inside a district. EFS is very much like shared stockpiling which can be gotten to from various accessibility zones inside a district. This filesystem can be gotten to by various process administrations like Amazon EC2, Amazon Lambda, and Amazon ECS. To get to the filesystem, these figure administrations should be in a similar accessibility zones in which the filesystem is sent off.
As Amazon EFS is a serverless help, you don’t have to deal with the filesystem, and it increases to Petabytes consequently without disturbing the application. You just compensation for the capacity your filesystem utilizes. Amazon EFS upholds NFSv4.1 and NFSv4.0 conventions, so you can interface with the filesystem utilizing these conventions. In this blog, we will make a filesystem traversing various accessibility zones. Then, at that point, we will get to this made flexible record framework by mounting it on EC2 cases in various accessibility zones.
Making Amazon EFS
From the AWS the executives control center, search and go to the EFS.
Go to the File framework from the menu on the left side.
Click on the Create record framework button to make another Elastic File System.
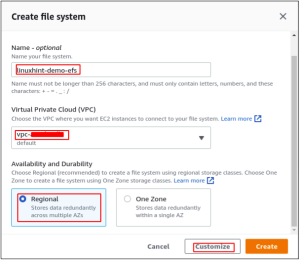
It will open a spring up requesting the subtleties of the Elastic File System. Enter the name of the flexible record framework to be made and select the VPC wherein the document framework will be made. For accessibility and sturdiness, select the Regional choice. It will make the document framework in various accessibility zones of the Region. Subsequently, the document framework will be open from these accessibility zones.
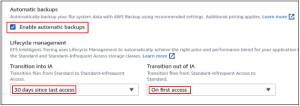
Empower the mechanized reinforcements of the versatile record framework by checking the Enable programmed reinforcements box. It will consequently make the reinforcements of your versatile record framework utilizing the AWS reinforcements administration. Life cycle the board can be utilized to save costs by turning the information into various capacity classes. The capacity evaluating for IA (inconsistently got to) class is not exactly that of the standard one. On the off chance that a record has not been gotten to for 30 days, the document will be moved to the rarely gotten to class to save cost.
There are two execution modes accessible in the flexible record framework that are General Purpose and Max I/O. Universally useful mode is utilized for most use cases, and it keeps the harmony among execution and cost, while the Max I/O is utilized where execution is the essential key.
The Throughput mode can be chosen in light of the size of every exchange. The Bursting mode scales the throughput with the size of the record framework, while Provisioned mode can be utilized to set the particular worth of throughput.
Presently go to the following page to design network access. Select the VPC and mount target accessibility zones and subnets from where the filesystem will be available. This filesystem will be available from the EC2 cases sent off in determined subnets just with the accompanying organization settings. The security gathering of the filesystem is different for each subnet.
On the following page, it will request the discretionary filesystem strategy. Skirt this step, survey, and make the flexible document framework.
Designing security bunches for EFS
While making the flexible record framework, on each mount focus on, a security bunch was joined. To get to the flexible record framework, a standard should be added to the security gathering to permit inbound traffic on the NFS port. From the EC2 console, go to the Security bunches segment.
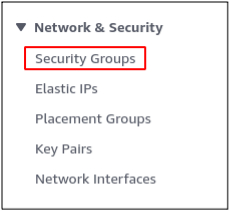
Select the security bunch you appended to the mount focuses while making the versatile document framework and alter the security bunch inbound guidelines.
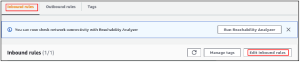
Add a standard to permit inbound traffic on the NFS port (2049) from the confidential IP locations of the EC2 occasions. The inbound rule is designed for this demo to permit inbound traffic on the NFS port from all over.

Save the recently made inbound rule to the security bunch, and the filesystem security bunch is designed.
Mounting EFS on EC2 occurrence
In the wake of making the flexible record framework, presently mount this document framework on EC2 occurrences. For this, EC2 examples should be in the equivalent subnets in which mount focuses for EFS are made. For this demo, the mount focuses for the filesystem are made in the subnets of us-east-1a and us-east-1b accessibility zones. Sign in to the EC2 occurrence over SSH and introduce the Amazon EFS client on the EC2 case.
ubuntu@ubuntu:~$ sudo apt update -y
ubuntu@ubuntu:~$ sudo apt install git binutils -y
Presently clone the archive, including amazon efs utilities from Github.
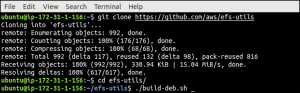
ubuntu@ubuntu:~$ git clone https://github.com/aws/efs-utils”>https://github.com/aws/efs-utils
Go to the cloned index and assemble the amazon-efs-utils.
ubuntu@ubuntu:~$ cd efs-utils
ubuntu@ubuntu:~$ ./build-deb.sh
Presently update the stores and introduce the amazon EFS client utilizing the accompanying order.
ubuntu@ubuntu:~$ sudo apt update -y
ubuntu@ubuntu:~$ sudo apt install ./build/amazon-efs-utils*deb -y
Subsequent to introducing the EFS client on the EC2 occasion, duplicate the flexible record framework ID to mount the document framework on the EC2 example.
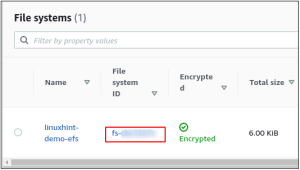
Make a registry and mount the flexible document framework on the index utilizing the accompanying order.
ubuntu@ubuntu:~$ mkdir ~/efs-mount
ubuntu@ubuntu:~$ sudo mount -t efs -o tls <file_system id>:/ efs-mount
![]()
Presently the versatile filesystem has been mounted on the EC2 occurrence and can be utilized to store information. This filesystem can likewise be gotten to on an EC2 occasion in the us-east-1b accessibility zone by following the above move toward mount the record framework.
A flexible record framework is a serverless common filesystem gave and oversaw by AWS, which can be gotten to in various accessibility zones. It very well may be utilized to divide the information among various mount focuses in various accessibility zones. Each mount point has its own security bunch on EFS, so a particular accessibility zone can be hindered to get to the filesystem by designing the security bunch. This blog makes sense of arranging and getting to the Elastic File System by mounting it on an EC2 case.
